How to hide Nginx version in http headers: A guide
When setting up Nginx web servers, security plays a key role. One important aspect is minimizing the information that the server reveals in HTTP headers. By default, Nginx sends information about its version in the Server header, which can be a clue for attackers.
In this article, we will look at how to remove Nginx version display to improve the security of your server.
The article on the page is based on my many years of experience with this technology and is presented to you as a small instruction, but if you want to get acquainted with it in more detail, then I recommend you go to the official documentation on Nginx.
By default, the NGINX web server sends the NGINX version number to the user.
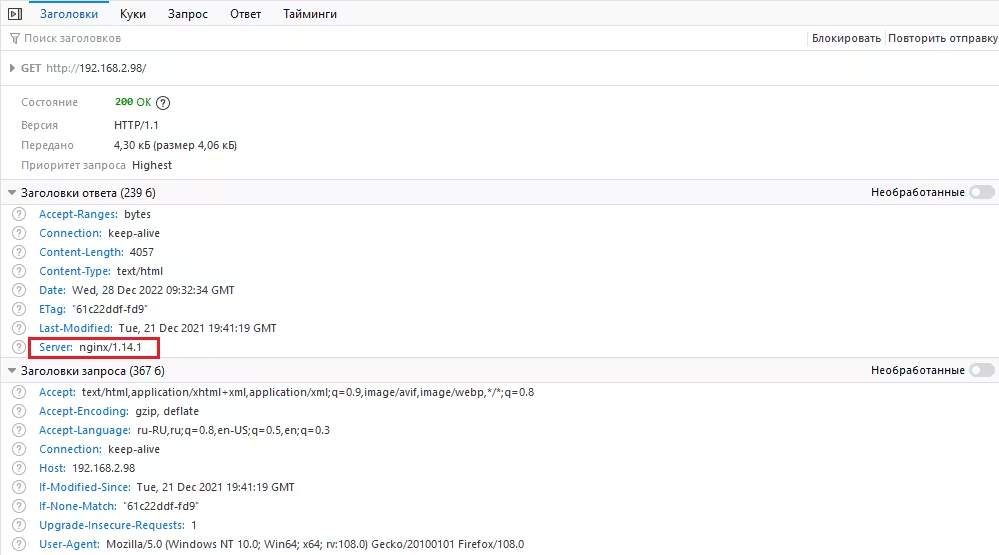
As we can see, NGINX sends a header called Server and this header contains the version number, this information needs to be hidden.
To hide the NGINX version number, you need to add the server_tokens parameter with the value off to the http directive in the main NGINX web server configuration file. The main NGINX configuration file is located at /etc/nginx and is called the nginx.conf file.
Open the file with any text editor convenient for you.
$. sudo vim /etc/nginx/nginx.conf
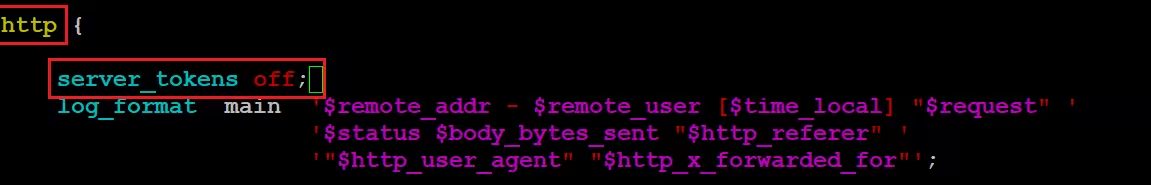
Add the server_tokens parameter.
http {
server_tokens off;
}
After we have added the parameter, we now need to restart the NGINX web server using the following command:
$. sudo service nginx restart
Reload the website page and check.
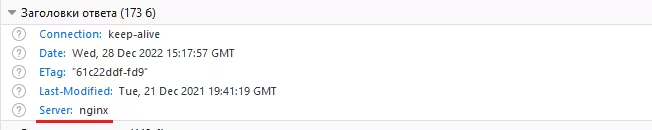
As we can see, the Server parameter now does not contain any confidential information that could help an attacker harm your site.
Hiding the Nginx version in HTTP headers is an important step in securing your web server. Setting the server_tokens parameter allows you to minimize the disclosure of unnecessary information about the system. Although this is not a panacea for all threats, such a measure complicates the task of attackers, reducing the risk of successful exploitation of vulnerabilities.
