How to disable root login via SSH in Linux: Quick guide
One of the key steps in securing Linux servers is to restrict access to the root account via the SSH protocol. This highly privileged account is often targeted by hackers because it allows them to execute any commands without restrictions.
Disabling remote root login not only makes life more difficult for attackers, but also encourages the use of more secure system management practices, such as logging in as a limited user and using sudo commands.
In this article, we will look at how to disable authorization on a Linux server using the root account via the SSH protocol so that your server remains secure.
So, there is a very simple way to disable the ability to log in via the root account to the system, for this we need to edit the main SSH configuration file called sshd_config. The file is located in the /etc/ssh directory.
Open the sshd_config file for editing with the command:
$. vi /etc/ssh/sshd_config
Find the PermitRootLogin parameter, remove the comment sign and change the parameter value from yes to no.
PermitRootLogin no

Save the changes.
After we have changed the parameter values, we must restart the SSH service for our changes to take effect.
To restart the SSH service, use the command:
$. systemctl restart sshd
Now when we try to log into the server via root in a new session, we will get the error Access denied.
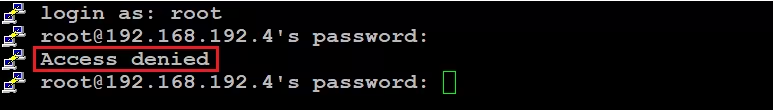
To get everything back, you need to change the PermitRootLogin parameter from no to yes in the main sshd_config file and restart the SSH service.
Disabling remote root login via SSH is an important step towards improving the security of your Linux server. Don't forget about other security measures, such as using complex passwords, setting up SSH keys, restricting access by IP addresses, and regularly updating the system. A comprehensive approach to server protection is the key to stable and secure operation of your applications and data.

